Introduction
In the intricate tapestry of the digital world, where data flows ceaselessly across networks, ensuring the integrity and security of Internet routing is paramount. Yet, the Border Gateway Protocol (BGP), the backbone of Internet routing, has long been confronted with vulnerabilities that expose it to manipulation and hijacking. Here comes the Resource Public Key Infrastructure (RPKI) – a cryptographic framework designed to fortify BGP and safeguard Internet routing against malicious actors.
Quick Recap on how the Border Gateway Protocol (BGP) operates
BGP is the protocol that interconnects the backbone of the Internet. It can be thought of as a GPS navigation system for the Internet. Just as a GPS guides you through different routes to reach your destination based on real-time traffic and road conditions, BGP helps routers determine the most efficient paths for data packets to travel across the Internet. It exchanges routing information between networks (autonomous systems) similar to how a GPS communicates with satellites and other GPS devices to provide accurate navigation directions. Ultimately, BGP ensures that data reaches its intended destination by dynamically mapping out the best routes available at any given time.
At its core, BGP operates on the principle of exchanging routing information between different Autonomous Systems (ASes), which are networks operated by distinct entities such as Internet Service Providers (ISPs) or large organisations. These ASes use BGP to communicate and decide on the best paths for routing data packets across the global network.
Routers advertise their available routes to neighbouring routers using BGP messages. These messages contain information about reachable IP prefixes and the paths to reach them. Neighbouring routers then use this information to update their routing tables and determine the most optimal paths for forwarding traffic toward the destination IP addresses.
The Problem Unveiled
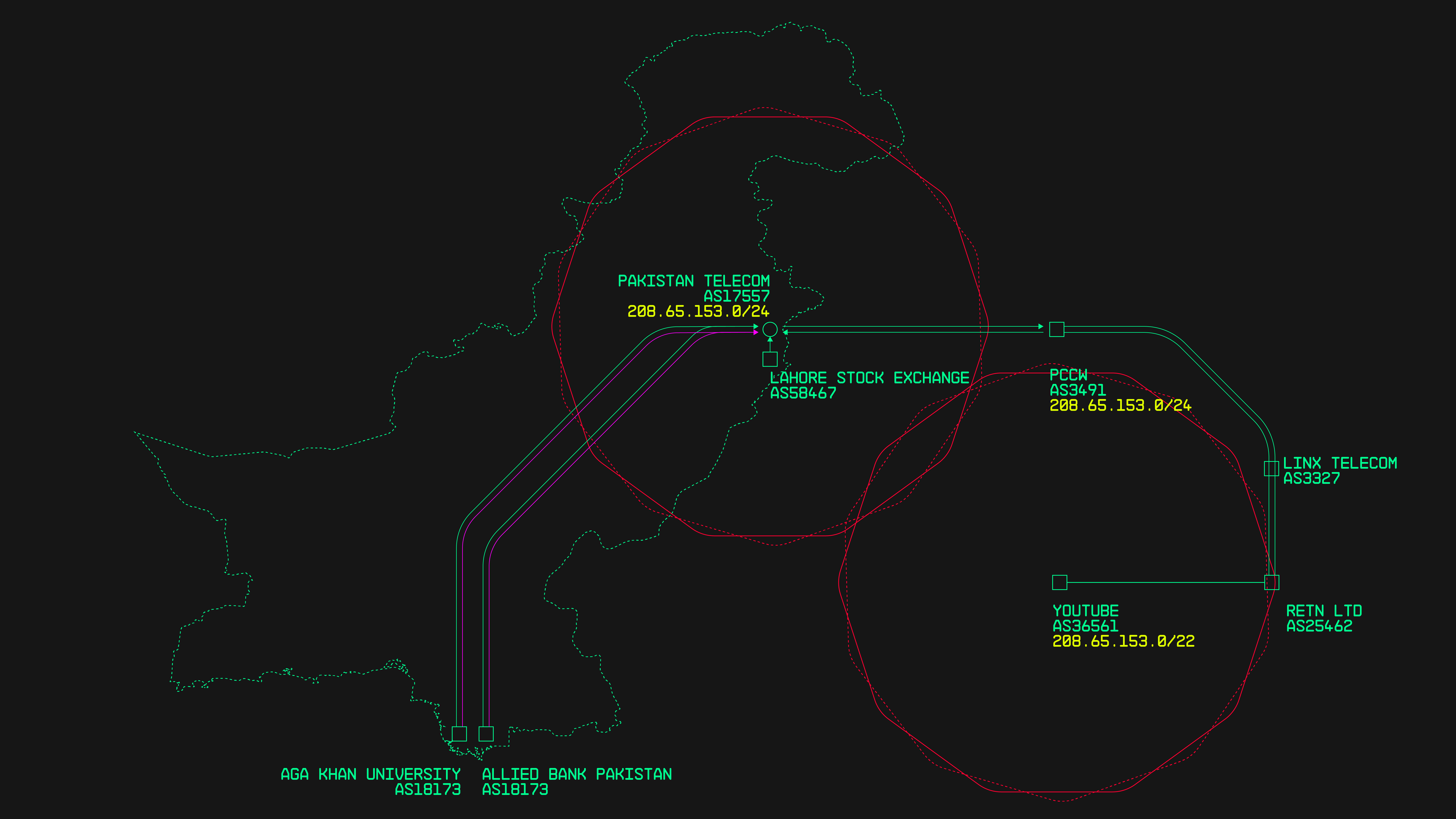
Illustration of the Pakistan Telecom hijack of YouTube in 2008
Picture a scenario where a rogue entity infiltrates an Internet Service Provider's network, deceitfully announcing false routes for IP prefixes. Suddenly, legitimate traffic is diverted to unwanted destinations, causing chaos and compromising the confidentiality, integrity and availability of online services. This insidious phenomenon, sometimes referred to as BGP hijacking, underscores the critical need for robust security measures to protect Internet routing.
You must think this is an aggravation, right?
Hold onto your socks for a second and delve into the story about to unfold...
In February 2008, to execute an order passed by the Government, Pakistan Telecom erroneously announced a BGP route, redirecting YouTube's traffic to its own servers. Unfortunately, the upstream providers on receiving the route accepted it without verification and then passed the information along, thus propagating the wrong route around the Internet, until almost everyone using the Internet believed facebook had moved its servers into a Pakistani network. The blunder not only took down YouTube, but also choked the Pakistani ISP, which was quickly deluged with millions of requests from Youtube users.
Before this event, similar incidents have occurred and are still occurring, among others we have:
- Read the incident of AS7007, that occurred in April 1997. (https://archive.nanog.org/mailinglist/mailarchives/old_archive/1997-04/msg00444.html)
- In 2004, a Turkish ISP called TTNet accidentally advertised incorrect BGP routes to its neighbours. These routes claimed that TTNet itself was the best destination for all traffic on the Internet.
- On January 22, 2006, Con Edison erroneously announced Martha Stewart prefixes, thus redirecting Internet traffic intended for Martha Stewart Living Omnimedia to its own servers.
- In April 2018, attackers deliberately created bad BGP routes to redirect traffic that was meant for Amazon’s DNS service. The attackers were able to steal over $100,000 worth of Bitcoins/cryptocurrency by redirecting the traffic to themselves.
The following BGP monitoring website can provide you with insights on ongoing BGP activities.
Existing solutions: IRR, filtering, RPKI, BGPsec
Traditionally, network operators have employed trust-based mechanisms like peer agreements and manual route filtering to mitigate the risks of BGP hijacking. While effective to a certain extent, these solutions are inherently limited, relying on human oversight and cooperation to uphold routing integrity. As the scale and complexity of Internet routing continue to expand, the need for a more resilient and automated approach becomes increasingly apparent.
One such resilient solution is filtering using the information available in the Internet Routing Registry (IRR). The IRR is a public database of routing information made available by Regional Internet Registries (RIR) and third party vendors. The information in the IRR says which ASN can originate a prefix. Cautious network operators use this data to inform their routing decisions. This solution has some limitations with data not systematically maintained due to third parties in the game.
The second advanced solution relies on the Resource Public Key Infrastructure (RPKI) to cryptographically authenticate routing information. In this blog and in subsequent articles, we will explore deeply this solution, stay on the ride while we take you deeply on how to secure your prefixes and Internet Routing with RPKI.
Border Gateway Protocol Security (BGPsec) is another advanced solution, that is a security extension of the BGP defined in RFC 8205. In BGPsec, the AS_PATH attribute is replaced with a new BGPsec_Path attribute, thus providing a means to cryptographically verify routes received from peers.
In this blog, we will have a quick overview of RPKI, as a solution to mitigate BGP vulnerabilities.
RPKI: Understanding the Basics
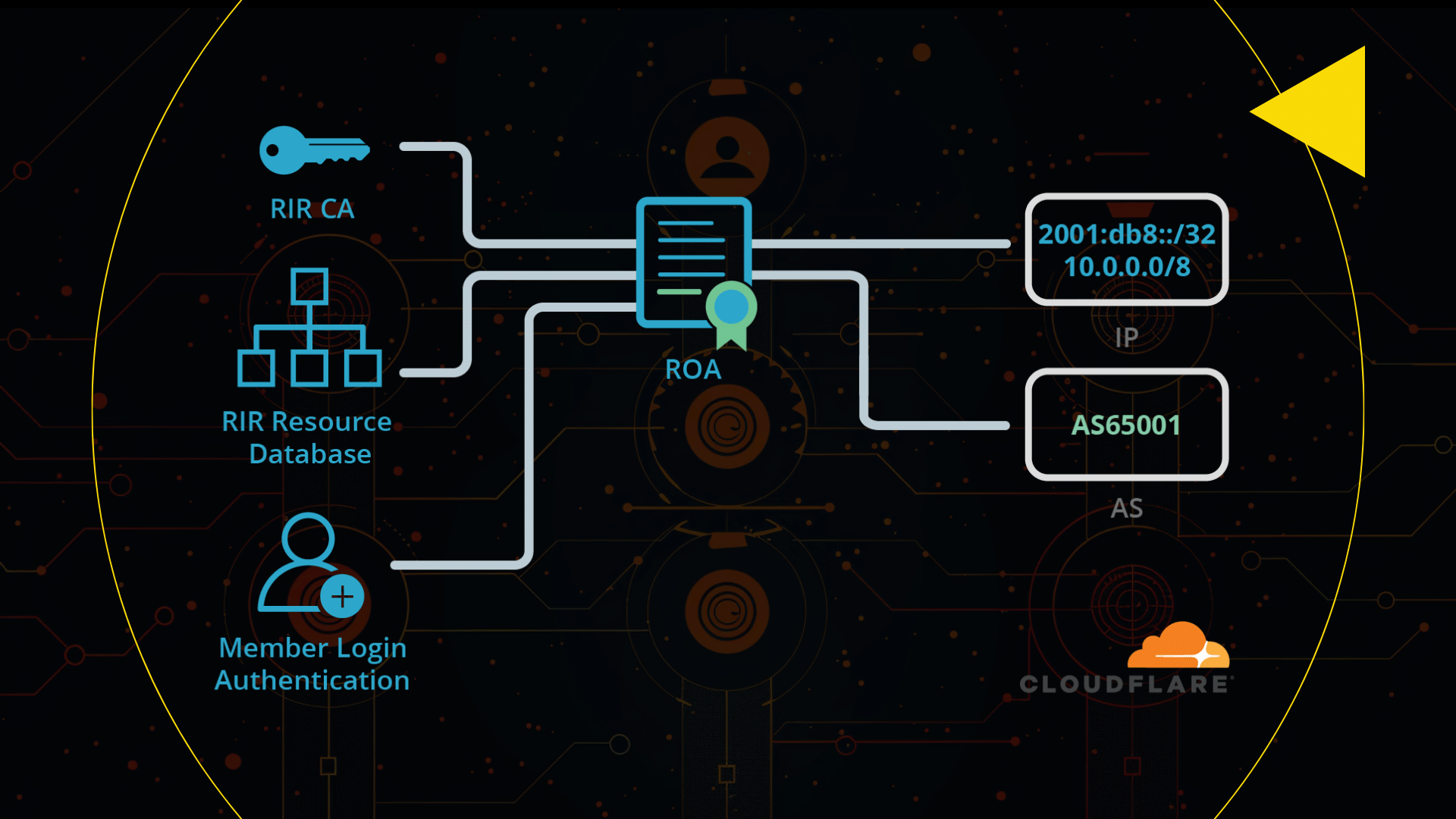
At its core, RPKI is a system built on the principles of public-key cryptography, aimed at enhancing the security of BGP routing. It works by associating a route (ASNs + IP) with cryptographic keys and digital signatures, providing a means to authenticate the legitimacy of route announcements. By leveraging cryptographic proofs, RPKI enables network operators to verify the validity of routing information and detect unauthorised BGP announcements.
By default, BGP routers receiving routes from other routers have no means to verify these routes.
Think of the RPKI system as a passport and visa control system for Internet traffic.
In this analogy, routing information is like a destination or a country on the Internet. Just as travellers need valid passports and visas to enter specific countries legally, Internet routers need valid cryptographic certificates and Route Origin Authorisations (ROAs) issued by RPKI to announce and validate IP prefixes.
The cryptographic certificates act as passports that verify the identity of IP address holders, while ROAs act as visas that authorise the legitimate origin of IP prefixes. Without the correct "passport" (cryptographic certificate) and "visa" (ROA), Internet routers cannot securely announce routes to specific destinations (IP prefixes), preventing unauthorised traffic flow and ensuring that data packets reach their intended destinations securely and efficiently.
With RPKI enabled, network operators and routers act as vigilant border control agents, verifying the legitimacy of route announcements before storing and propagating such information, thus preventing unauthorised traffic from entering or leaving specific "countries" (IP prefixes) on the Internet.
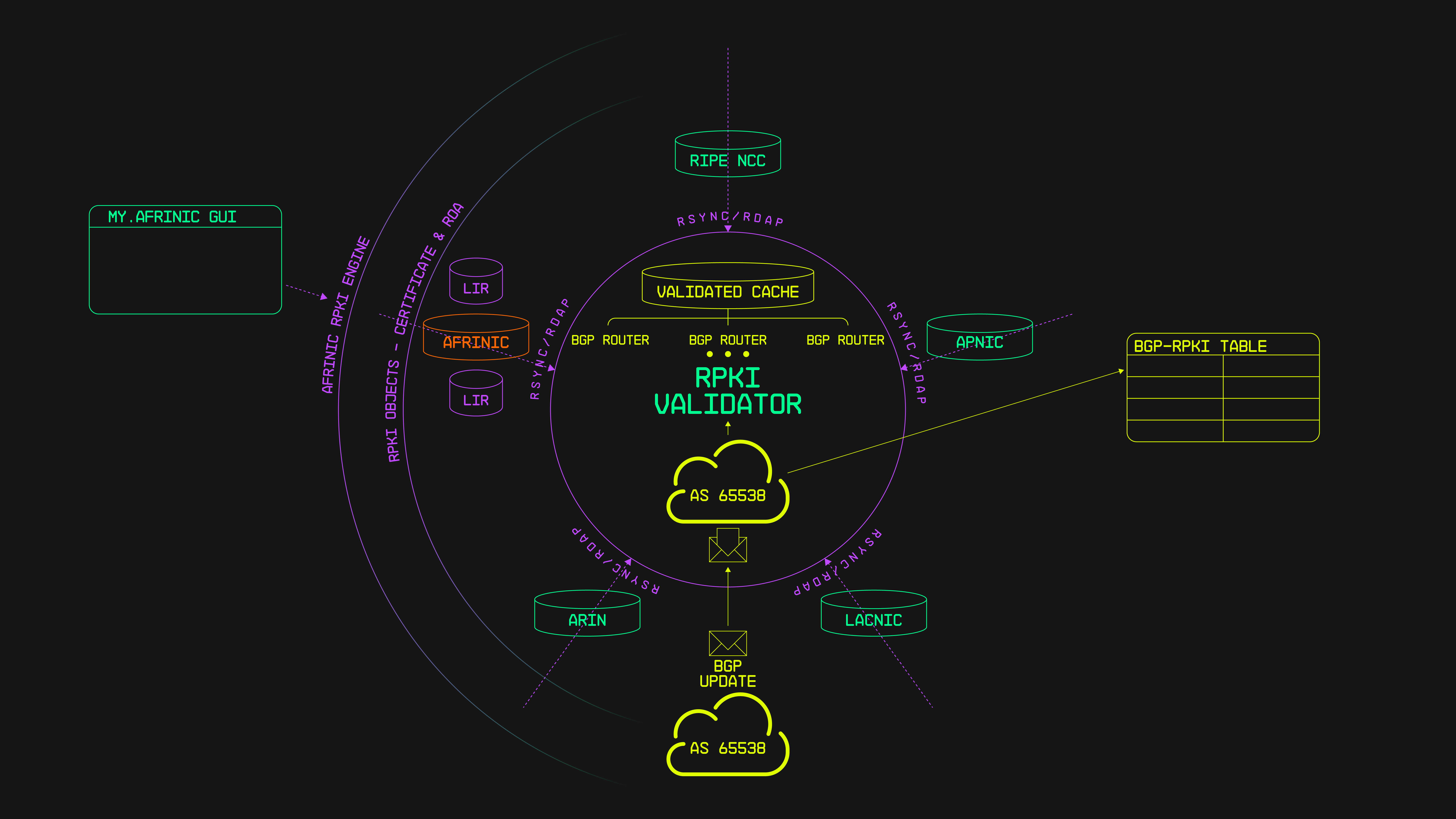
How RPKI Works
RPKI operates on a hierarchical model, wherein Regional Internet Registries (RIRs) serve as the top-level authorities responsible for managing Internet number resources. These resources include IP address blocks and Autonomous System Numbers (ASNs), which are essential components of Internet routing. RIRs issue cryptographic certificates to resource holders, binding their IP address allocations to cryptographic keys. These certificates are then used to generate Route Origin Authorisations (ROAs), which specify the legitimate origins of IP address prefixes.
Why RPKI Matters
The adoption of RPKI brings a multitude of benefits to the Internet ecosystem. By providing a mechanism to validate the authenticity of route announcements, RPKI helps prevent BGP hijacking and route leaks, thereby enhancing the security and stability of Internet routing. Additionally, RPKI enables network operators to assert control over their routing policies, ensuring that traffic flows along intended paths and minimising the risk of misconfigurations or malicious activities.
Wrap up
In conclusion, RPKI represents a significant advancement in the realm of Internet routing security. By harnessing the power of cryptography, RPKI offers a standardised and scalable solution to the persistent challenges posed by BGP vulnerabilities. As we continue to navigate the complexities of the digital landscape, the adoption of RPKI stands as a crucial step towards building a more secure, resilient, and trustworthy Internet infrastructure.
PS: In subsequent articles of this series, we will delve into the intricacies of RPKI deployment, explore practical applications and discuss best practices for implementation. Join us on this journey as we unravel the mysteries of RPKI and unlock the potential for a safer, more secure digital future.




